Data Security Threats to the Internet of Things
 Global adoption of broadband connectivity is fueling the growth of the Internet of Things (IoT), with 773 million broadband households anticipated worldwide by the end of 2015. By the end of 2019, broadband households will total 972 million households, with over half of those in China. In North-America and Western Europe, 50% of broadband households own at least one connected entertainment device, smartphone, or tablet. Asia-Pacific will achieve 50% adoption rates of these devices by 2018. Connected wearable devices are anticipated to reach 50% adoption by broadband households in North-America by 2018 and in Western Europe by 2019.
Global adoption of broadband connectivity is fueling the growth of the Internet of Things (IoT), with 773 million broadband households anticipated worldwide by the end of 2015. By the end of 2019, broadband households will total 972 million households, with over half of those in China. In North-America and Western Europe, 50% of broadband households own at least one connected entertainment device, smartphone, or tablet. Asia-Pacific will achieve 50% adoption rates of these devices by 2018. Connected wearable devices are anticipated to reach 50% adoption by broadband households in North-America by 2018 and in Western Europe by 2019.
The growth of connected devices and the IoT prompts serious consideration of data privacy and security, two distinct concepts. Data privacy is considered from the user’s perspective, whose personal information may be at risk of compromise. Data security, on the other hand, is considered from the perspective of the providers of products and services who gather many types of information in their efforts to create value for the company and the consumer.
With consumer data passing through and stored throughout the IoT ecosystem, the security challenge demands vigilant best practices and due diligence by every stakeholder. While security professionals from various industry vantage points each have their own priorities, the Open Web Application Security Project (OWASP) identified 10 of the top IoT threats in 2014:
- Insecure Web Interface – Weak or plain text credentials exploited by enumerating accounts until access is granted.
- Insufficient Authentication/Authorization – Vulnerability at the web, mobile, or cloud interfaces due to poor password requirements, poor transmission of credentials, failure to require re-authentication for sensitive data, or lack of periodic password resets.
- Insecure Network Services – Vulnerability from open network ports with DoS or UPnP vulnerabilities or vulnerabilities related to UDP services or buffer overflow and fuzzing attacks that cause device to crash.
- Lack of Transport Encryption – Caused by information being passed in plain text rather than using transport encryption for data moving across networks, mobile applications and cloud services.
- Device Level Privacy Concerns – Data can be compromised by anyone with access to the device, the network the device is connected to, and the cloud connection.
- Insecure Cloud Interface – Easy-to-guess credentials are used or account enumeration is possible through subjecting exposed usernames to brute force or dictionary attacks.
- Insecure Mobile Interface – May occur at the point of connection of a mobile device with a wireless network.
- Insufficient Security Configurability – Present when users of the device have limited or no ability to alter its security controls.
- Insecure Software/Firmware – The lack of ability for a device to be updated when vulnerabilities are detected presents a security weakness.
- Poor Physical Security – When an attacker can disassemble a device to access the data storage medium.
The greatest challenge to securing the IoT is that no entity is in charge of securing it. Developers, manufacturers, and consumers each have their roles to play. Smart companies will develop smart strategies that will deliver on their brand promises to consumers for an IoT that is, collectively, as smart and secure as the devices that comprise it.
For more information on data security and privacy in the IoT, see my industry report Privacy and Big Data: Safeguarding Consumers.
Further Reading:
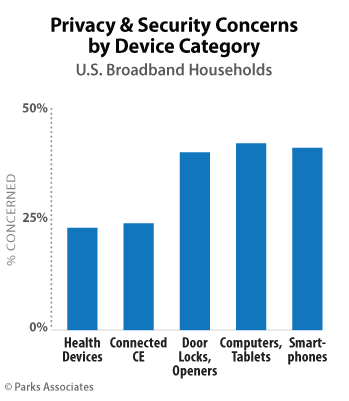
- 50% of broadband households have privacy or security concerns about smart home devices
- Value-Added Services, Privacy Innovations Will Help IoT Become Future-Proof
- Leading with Data: Unlocking the Value of Connected Products
Next: With Big Data Comes Big Responsibility: Consumer Vulnerability to Data Attacks
Previous: The Smart Home is the Next Big Data Frontier
Comments
-
Be the first to leave a comment.
Post a Comment
Have a comment? Login or create an account to start a discussion.