IoT Devices Exploited by Botnets for Unprecedented Hack
 Last week, half the Internet was shut down by an unprecedented hacker attack on the servers of Dyn, a major U.S. domain name server (DNS) host for media companies such as Netflix, Facebook, and Twitter. The hackers used what is commonly referred to as a distributed denial of service (DDoS) attack. DDoS attacks basically bombard a server with so many requests it has to slow down or shut down because it can’t handle the traffic. Even with sophisticated DDoS protection software in place, major hosting services can be overwhelmed by the sheer scale and, in this case, multiple waves of assaults.
Last week, half the Internet was shut down by an unprecedented hacker attack on the servers of Dyn, a major U.S. domain name server (DNS) host for media companies such as Netflix, Facebook, and Twitter. The hackers used what is commonly referred to as a distributed denial of service (DDoS) attack. DDoS attacks basically bombard a server with so many requests it has to slow down or shut down because it can’t handle the traffic. Even with sophisticated DDoS protection software in place, major hosting services can be overwhelmed by the sheer scale and, in this case, multiple waves of assaults.
What was more uncommon was the way the distributed part worked. This time, hackers exploited IoT devices like networked cameras, Wi-Fi routers, and smart lighting systems by using a malicious botnet that exploits weaknesses in the embedded source code used by many IoT devices. The compromised devices then issue what looks like legitimate service requests from tens of millions of IP addresses at the same time. In other words, hackers manipulated an army of devices to act as their minions. The source code for one suspected botnet, Mirai, was recently released by hackers on the HackForum website for use by anyone online with malicious intent. Not only does Mirai exploit weaknesses in the Linux-based telnet remote connection protocol, it also encrypts the data packets passing between the compromised devices and the servers they communicate with. The encryption makes detection of malicious activity even harder for security providers.
The motives behind DDoS attacks can be varied. They are often used as ransom attacks to extort payment. They can be probes of infrastructure vulnerabilities as groundwork for future hacking events of even larger scale. They can be state-sponsored attacks as part of an even larger cyberattack strategy against the economies of rival nations.
So what does this mean for various players in the IoT and the consumers they seek to serve?
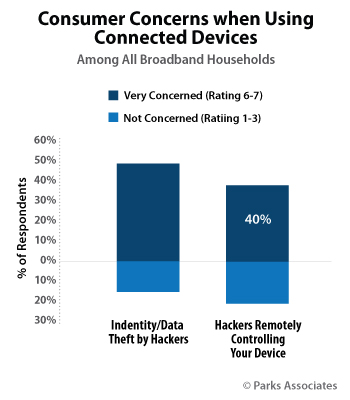
At Parks Associates, we know that 76% of broadband households express high levels of concern about security/privacy when using any of their connected devices. High levels are indicated by a “very concerned” rating of 6 - 7 on 7-point scale. Forty percent of broadband households are specifically concerned about hackers remotely controlling their devices. While only 3% of broadband households reported that hackers had gained access to their device in the 12 months preceding Q3 2015 that amounts to almost 3 million U.S. households. Given what transpired last week, we expect to see that number rise substantially in the coming year. Consumer concerns already play a role in slowing adoption of connected devices. Consumers, however, may never know if their device is actually used in a hacking event. In some documented cases, the infected video cameras, for instance, still function normally, albeit a bit slower.
Justifying consumer concerns, IoT devices are attractive to botnet-based hackers precisely because they are typically much less protected than computers, tablets, and smart phones. The reasons they are less protected include: device constraints on board memory, processing power, and simplified operating systems that preclude embedded antivirus and malware protection. At the same time, IoT devices such as networked cameras possess significant-enough processing power and high-speed Internet connectivity which make them powerful weapons in hacker warfare. The cumulative bandwidth of internet-accessible cameras has previously been used to launch attacks of 400 Gbps in DDoS attacks. Given the verified vulnerability of IoT devices, security analysts advocate the use of components and update processes that are sufficient to provide security protection throughout the product lifecycle. Every third-party playing a role in delivering services must also be carefully vetted for best practices in security.
Finally, the gap between consumer reported concerns and consumer security practices continues to evidence a disconnect that only consumers themselves can remedy. As long as consumers do not undertake basic security practices, such as replacing default factory settings with customized passwords, and changing credentials frequently, there is only so much manufacturers can do. Manufactures are best positioned by baking as much security into devices and automating security processes as much as they can, and then continually educating consumers on best practices.
Further Reading:
- Best Practices for IoT Security and Privacy
- Delivering Peace of Mind: Connected Home Devices & Sensors
- The Real Costs of a Corporate Data Breach
Next: Consumer Strategies and Use Cases for Virtual and Augmented Reality
Previous: Sony’s launch of PlayStation VR bolsters virtual reality market
Comments
-
Be the first to leave a comment.
Post a Comment
Have a comment? Login or create an account to start a discussion.