Apple Removes Screen Time Apps: A Competitive Strategy?
Last weekend, the New York Times reported that Apple removed or restricted 11 of the 17 most downloaded apps that help consumers manage the time they spend on devices (screen-time tracking apps) and apps that provide parental control. The removal of these apps comes on the heels of the launch of Apple’s new Screen Time feature, which the company launched as part of iOS 12. Apple’s Screen Time feature has functions similar to the apps that the company removed or restricted from the App Store. The feature tracks users’ phone usage habits and allows consumers to set limits on the amount of time they spend using specific apps. The app also allows parents to supervise the amount of time kids spend on their phones.
According to the article in the New York Times, Apple’s Screen Time app is more restricted in functionality compared to the third-party apps the company removed from its App Store, prompting many to believe the apps were removed as a competitive strategy. However, Apple responded to these claims stating that the apps were removed because the privacy and security of the apps’ users were at risk. Apple added that these companies were leveraging Mobile Device Management (MDM) solutions, which allow third party apps to not only have control over consumer devices, but also provide access to sensitive information including user location, app use, email accounts, camera, and browsing history. This is a policy violation according to Apple, and developers found in violation of the policy were given 30 days to update their apps to avoid interrupted access to the App Store.
Do security and privacy issues serve as a barrier to product adoption?
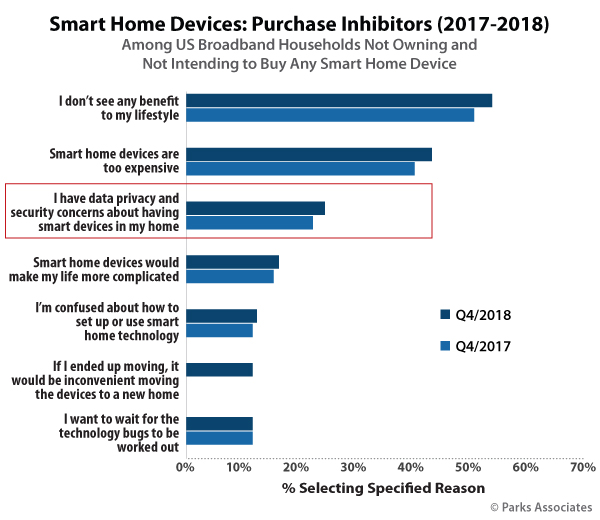
User privacy and security is an increasingly important topic in the world of connected technology. High security and privacy concerns among consumers have led many to question whether or not these concerns serve as a legitimate barrier to adopting new connected technologies. Parks Associates research indicates that 25% of consumers who report that they do not intend to purchase smart home devices will not purchase the devices due to concerns about security and privacy, a slight increase from 2017. Other industry players posit that consumer concerns about security and privacy will not affect device adoption and cite stable growth in the smart home market as evidence of this.
Is security and privacy protection a competitive differentiator?
Another question worth exploring is how much security and privacy serve as competitive differentiators among connected technology brands. Along with the aforementioned punitive measures executed by Apple, it was recently reported that Google locked Nest users out of their accounts to prompt them to make their login credentials more secure. These measures taken by Google and Apple are geared at protecting their brands from repercussions stemming from a breach of security associated with their products and services. However, given that these measures directly affect a large number of consumers, the resulting publicity promotes the brands as dedicated to protecting customers’ security and privacy—which should increase brand trust and appeal. Recent issues with Facebook demonstrate that security and privacy issues can directly affect product and service adoption. NBC News reported that consumer trust in Facebook fell by 66% following the Cambridge Analytical scandal. A Ponemon survey following the scandal found that 9% of Facebook users stopped using the service altogether after the scandal. Another 31% reported likelihood to stop using the service or use it less than in the past.
Parks associates will explore consumer security and privacy issues in the connected home in a panel titled Data Security and Privacy: Empowering Consumers at its CONNECTIONS event, taking place May 21 to 23 in San Francisco, CA.
Further Reading:
- AI, Machine Learning, and Data Analytics in the Smart Home
- 77% of consumers are very concerned about someone hacking their online service
- Broken Trust: Facebook Data Exposure Reinforces Consumer Privacy Concerns
Next: Changing Dynamics of the Smart Home Create Opportunities for Service Providers
Previous: Data Privacy is Key Issue Highlighted by F-Secure at CONNECTIONS
Comments
-
Be the first to leave a comment.
Post a Comment
Have a comment? Login or create an account to start a discussion.